Analyze your data while the data is encrypted
FHE is a powerful cryptographic primitive that enables performing computations over encrypted data without having to decrypt any data or share access to any secret keys. Duality platform leverages this technology for running a wide range of computation: Encrypted queries, Analytics and ML train/inference. FHE is known as the most secure option for protecting data, however, it has limitation in terms of computation coverage and performance. Duality FHE is unique in a sense that it can run FHE computation on a wide range of algorithm while keeping the performance and resources needed practical.
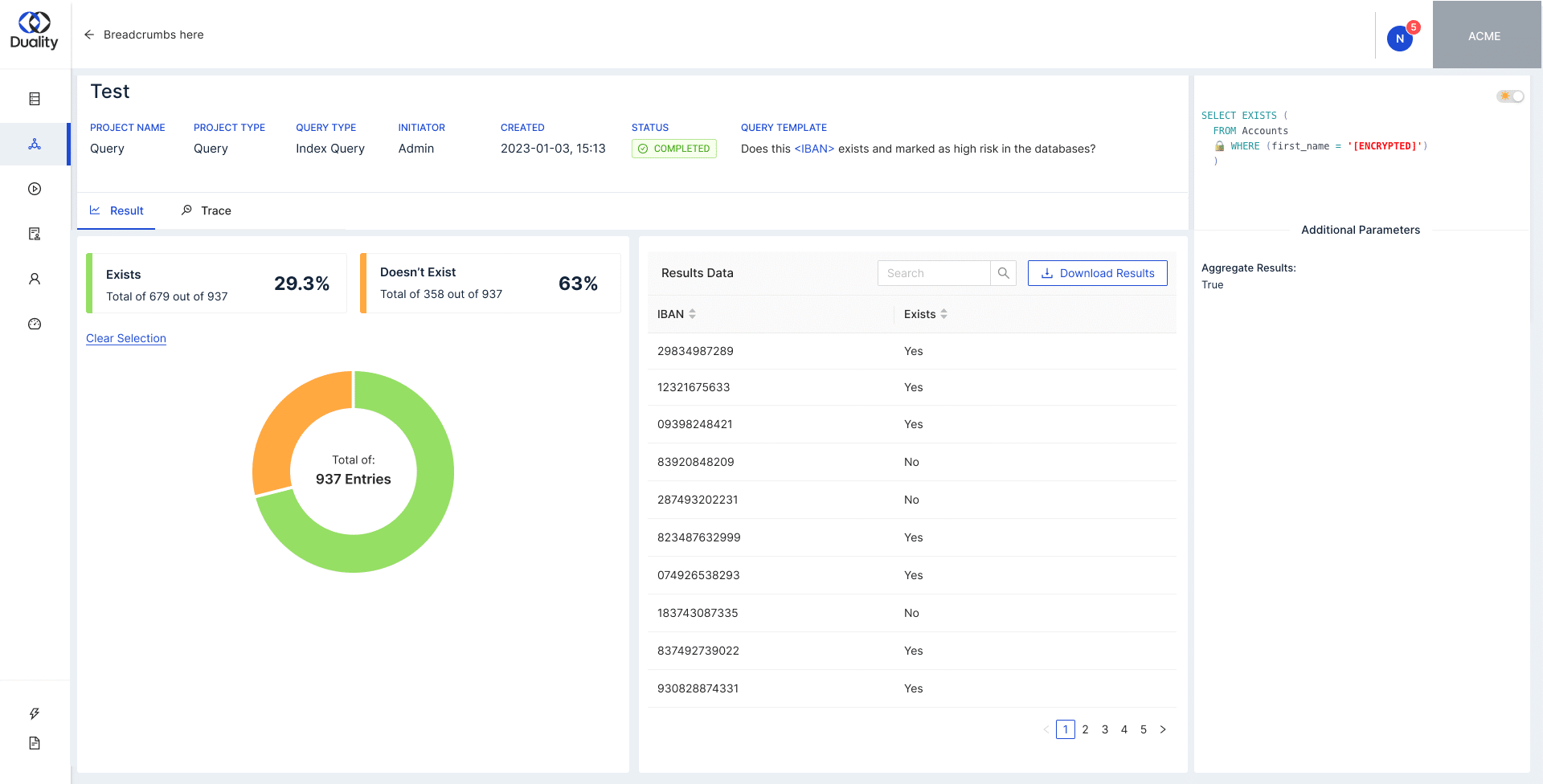

Run thousands of encrypted queries per second on lightweight machine

Built-in tools for aligning schemas, transforming data, and pre-processing for multiparty collaboration.

Post-quantum security protections against quantum computing attacks.
Ensure full control on your data, decide who accesses the data, which computations will run, at what frequency, and more.
Duality combines FHE and MPC in order to enable secure computation when multiple parties are involved (e.g. multiple parties want to create a share model)

Support popular models for training and inference such as linear & Logistic regressions, XGBoost as well as built-in analytics computation.
Improve AI/ML model performance by training, tuning and validating AI and ML models on encrypted data.
Optimize efficiency by working collaboratively across borders while meeting data privacy and residency requirements.
Analyze sensitive medical data across centers to gain deeper insights to speed research and discovery.
Access new high-value data sets in a privacy-protected and compliant manner.
Protect sensitive data and models while transitioning AI workloads to the cloud.
Apply third-party analytics and ML models to your sensitive data without exposing it.
Deliver personalized customer experiences and upsell with partners while preserving privacy.
Create new revenue sources from sensitive data while preserving privacy and regulatory compliance.
Maximize the value of sensitive, regulated, or confidential data.