USA PATRIOT Act Section 314(b) permits financial institutions, upon providing notice to the United States Department of the Treasury, to share information with one another in order to identify and report to the federal government activities that may involve money laundering or terrorist activity, including predicate offenses. I recently had the opportunity to participate in an exclusive roundtable discussion about 314(b) with financial regulators, other government agencies, and financial institutions of all sizes. Each participant contributed his or her own unique perspective on 314(b), the benefits and challenges of using it, and the main concerns and limitations that prevent full utilization of this important information sharing legislation.
This blog focuses on information sharing in the United States. It starts by simply explaining the legal intricacies of what information can be shared, how it can be shared, when it can be shared, and who can share it. It then will summarize the roundtable discussion and take a look into barriers institutions face in fully leveraging 314(b).
What is 314(b)?
Information sharing for AML/CTF purposes has long been allowed under Section 314(b) of the USA PATRIOT Act, which grants participants a safe harbor, and was enacted in response to the September 11, 2001 attacks against the United States. Since then, as 314(b) proved to be a successful program, regulators and government organizations around the world like FATF, FINTRAC, the FCA, and of course FinCEN, have continued calling for more information sharing and collaboration among regulated entities in order to better fight financial crimes and terrorism.
- Who may share information
- Financial institutions or associations of financial institutions may share information with each other
- What information can be shared
- There is no limitation to the type of information that can be shared, including personally identifiable information. This also includes information regarding individuals, entities, and organizations
- This information can be related to money laundering and terrorist financing, as well as to how the proceeds of predicate offenses, including fraud and cybercrimes, are used
- When information can be shared
- Importantly, organizations who share information under 314(b) are given a wide berth of when the safe harbor applies
- According to FinCEN, it is enough to simply suspect that activities may involve money laundering, terrorist activity, or the proceeds of a predicate offense – even if the specific activities or proceeds cannot be identified. This applies not only to transactions, but to attempts to transact or induce others to engage in transactions.
314(b) is Valuable Legislation, but Underutilized
The main purpose for convening the roundtable was to discuss the barriers to more comprehensive use of 314(b). This would allow the financial services industry to better leverage the law to prevent money laundering and terrorist financing. Overall, there was unanimous consensus that 314(b) is a very valuable piece of legislation that grants financial institutions an effective tool against these types of criminal activities. Many even stated that the data they get from the program is more valuable than what they receive from their own transaction monitoring systems. However, there was also agreement across the board that 314(b) is currently underutilized and therefore, it is still far from reaching its full potential. Some of the barriers to full utilization that participants raised include: resourcing, prioritization, quality, trust, scalability, regulatory clarity, and privacy.
Despite 314(b), Financial Institutions Still Hesitate to Share Information
Due to limited resources and the overhead it takes to respond to 314(b) requests, financial institutions give priority to investigating their own alerts and cases. In principle, there is a strong willingness to participate, but in practice this prioritization inevitably causes delays in responding to requests from other institutions. This imbalance in prioritization is one serious challenge with 314(b), and clearly demonstrates the need for appropriate incentives to collaborate and tools to enable efficiency.
An additional concern that came up was in regards to the legal ramifications. Although FinCEN interprets 314(b) as allowing information sharing on predicate offenses to money laundering and terrorist financing (like fraud, cyber crimes, and more), that does not mean that financial institutions completely accept this interpretation. This creates a gray area around exchanging information on predicate offenses, where some financial institutions follow this interpretation and others do not. In fact, many financial institutions expressed concern about information sharing in the case of suspected fraud, stating that if they receive an information request they believe is related to fraud, rather than having a clear link to money laundering, they would not respond. Further formal legal clarification (rather than interpretations) on precisely what information can be shared and under which circumstances will give financial institutions greater confidence that their activities are well within the letter of the law.
Another concern that was tabled was regarding what happens if something goes wrong when sharing information. In the event of a cyber attack or data breach that leads to exposure of shared data, the fallout in terms of reputational damage and lawsuits could be severe. If this happened on a large scale, it could even potentially spark blowback by congress and citizens jeopardizing the data sharing practice. Safeguarding against data misuse and scandal is critical to expanding the implementation of 314(b) (which is why I have advocated for decentralized data sharing, wherein a breach at one participant does not affect the entire system).
Ultimately the barriers and concerns holding back a full fledged implementation of 314(b) by all financial institutions can be whittled down to two competing values. On the one hand, governments are very motivated to tighten enforcement of AML and Counter Terrorist Financing (CTF) laws. AML/CTF legislation is one of the most important law enforcement tools against organized crime, human trafficking, and global terrorism. On the other hand, privacy is a pillar of the financial system, so finding an amicable trade-off between AML and privacy is much easier said than done. In short, practical solutions are needed that will make the process of participating in 314(b) more seamless and cost-effective in order to increase the law’s effectiveness – as well as address any potential privacy issues which may arise.
A Privacy-First Approach to Information Sharing
The way to do this is with a privacy-first approach. Privacy helps address all of the challenges everyone discussed: the quality of requests, issues surrounding trust, scalability, regulatory compliance, and data privacy. Viewed from the standpoint that privacy is an enabler, not an inhibitor:
- Privacy helps collaborate as a network, at scale – instead of 1:1, which is the case today and one of the major contributors to cost
- Privacy helps participants in data collaboration projects automate processes and create strong governance to manage capacity and workflow – in other words, enabling what I call “Privacy Enhanced Automation”
- Privacy helps ensure that trust is maintained between all participants as well as between participating institutions and regulators, where all participants can be sure that their data is safe
The Role of Privacy Enhancing Technologies (PETs)
US Government representatives at the roundtable suggested Privacy Enhancing Technologies (PETs) as a possible solution to the privacy versus efficiency issue – as long as there were rules enacted around governance. Several PETs, as our readers know, allow for insights to be derived from data while it is still encrypted, and for secrets to be shared between parties in zero-trust environments by leveraging advanced cryptographic techniques.
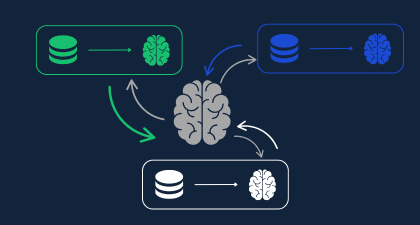
When applied properly, PETs can allow institutions, which are authorized to share information under 314(b), to do so confidently with the assurance that information is secure in the event of a breach – and without the use of the manual processes traditionally required to share the information. In this scenario, institutions can create a privacy-protected network for information sharing that not only protects the identities of the entities under suspicion, but also the identities of the financial institutions responding to requests. For example: if Bank A inquires about Entity X, Bank A will receive a list of anonymized “yes/no” answers – without revealing the specifics about what Banks B, C, and D responded.
Duality is proud to use PETs for this purpose. We are a 314(b) Association, meaning that any financial institutions registered for FinCEN’s 314(b) information sharing program may use Duality to share privacy-protected information on any entity or transaction that is suspected of involvement in money laundering, terrorist financing, or predicate offenses including fraud and cybercrimes.
For more information about 314(b) and using PETs to fight financial crime, read our financial crime one-pager.