Data is the foundation of the information revolution and the knowledge-based economy. The right data, in the right hands, at the right time, has become a highly valued commodity across industries. Data is at the root of uncovering new business opportunities and defining new and more innovative products., The tech giants of today have built their businesses and value on data versus goods—e.g., Google, Facebook, Twitter, and Airbnb.
Examples of Data Collaboration
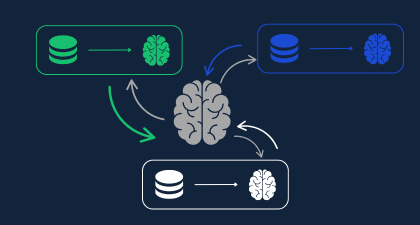
Data-driven enterprises are leveraging advanced data computational tools such as artificial intelligence and machine learning models to predict future demand and shape current buying patterns. However, enterprises frequently own only part of the data needed to build a complete and comprehensive picture, so they are pursuing data collaboration agreements with third parties. Enterprises across industries are collaborating around data sets created, curated, and owned by separate entities. For example:
- Drug development by pharmaceutical companies relies on clinical research and trials that aggregate patient data from a range of healthcare providers and institutions. Aggregated data needs to be analyzed by researchers while protecting the identity of patients. Quickly building large aggregated datasets drives faster time to market for new drugs, new revenue streams, and ultimately saves lives.
- Cloud services providers routinely combine data on cybersecurity threats and incidents from a wide array of individual customer organizations to assess overall risk, discover new attack vectors, and warn customers about emerging threats. Combining data from all customers allows them to quickly discover and respond to threats and reduces the likelihood of a compromising incident for all cloud customers.
- In a financial services firm, different departments sell varied financial products to the same customer. Data collaboration enables departments to understand the full extent of the bank’s overall relationship with any given customer, as well as identify opportunities for additional financial products. Aggregated data can also unlock the applicability of restricted services—e.g., wealth management services that require a minimum wealth level to be met. The business results include elevated customer affinity and revenue growth.
- After a merger or acquisition is completed, the newly combined enterprise has to act in unison as a single entity. Data collaboration enables the two previously separate firms to compare customer and prospect lists to identify overlaps for consolidation, as well as upsell and cross-sell opportunities based on the new value proposition. The business result is accelerated time to synergy.
Data Collaboration Agreements Built on Trust
When complete ownership and control of data by a single entity is not possible or feasible, enterprises have turned to legal agreements to govern collaboration on data with other enterprises.
Setting up a joint agreement between firms about the conditions under which confidential and sensitive data will be shared is a very common practice—and rightly so. Signing a data sharing agreement, or some other document that outlines how sensitive data must be protected, specifies in writing the types of data that will be shared, the consequences of knowingly or unwittingly sharing it with people who are not authorized to see it, and the ramifications if the conditions are breached. However, even the best data sharing agreement, contract or other document is built on the assumption of trust between the parties.
When trust works it offers a virtually unbreakable bond between people, but too often its fragile nature is destroyed by subterfuge, negligence, or innocent human error. NDAs, contracts, and intellectual property agreements do not keep sensitive data safe. What they do well is create a shared context of consequences and ramifications that activate if contractual terms aren’t met, but in terms of actually keeping sensitive data safe—they offer nothing. For example, contracts cannot guarantee that an employee authorized to work with the data won’t steal it, share it, or otherwise act outside of the original sharing intent. Any of those actions will trigger the consequences and ramifications in the contract, but the compromised data remains compromised, nonetheless.
Creating a shared legal context for data collaboration is a lengthy and labor-intensive process, especially when regulatory bodies must be informed, engaged, and convinced that the requisite safeguards are in place. Having an internal legal department review any proposed agreement is standard practice, and often external legal counsel is engaged for a second and more severe opinion. Along with regulatory approvals, anything that triggers legal review by internal or external counsel results in time delay and elevated cost. Trust is both slow and costly.
Time to Adopt a Privacy-Enhancing Technology?
Privacy-enhancing technologies (PETs) drive key business results faster, easier, and with less risk—and without the cost incurred for trust. Data can be shared between firms faster because lengthy legal processes to establish joint responsibilities and conduct third-party security reviews can be minimized. Data remains encrypted and therefore is never shared in a way that a human at the other party can make sense of it, effectively removing the threat of accidental or malicious breach. Since the data always remains protected , the risks of inappropriate usage fall away.
Privacy Enhancing Technologies offer significant value in data collaboration initiatives:
- Never lose control over the data you are responsible for
Data remains stored and encrypted where the organization wants it stored—with the preferred access and information governance controls in place. No file sharing sync or emailing of sensitive data occurs. A secure data hub is formed so data collaboration activities happen across data sets without removing decryption. When the data collaboration ends, there are no “return and destroy” conditions to enforce, no unprotected copies floating around in email inboxes, and no tidy up of a shared folder to carry out because no copies of the data were ever made.
- Data is always encrypted, even in use during collaboration
The same techniques that organizations use for encrypting data when it’s stored or in transit are used during data collaboration activities. Cryptographic representations of data elements in different sets are compared, not plain text values. This ensures privacy-by-design principles are always met, and that humans don’t get eyeball access to the data. Data Protection Officers and Chief Privacy Officers can sleep well at night assured they are compliant with regulations, and any meetings with regulators can be around coffee rather than compliance breaches.
- Wave goodbye to legal complexities shuttering data collaboration opportunities before they even begin
Legal complexities are simplified when data is shared while remaining encrypted. Since the risks of breach, malicious misuse, and nefarious activities are removed from the equation, the conditions under which separate fully encrypted data sets can be compared are simpler to define. New data collaboration projects can be established faster and easier. Insights on new business opportunities can be generated in a shorter time than what it used to take just to get an opinion from the internal legal team on whether doing so was legally possible.
- Regulatory challenges reduced or simplified
Data privacy regulations, of which there is a rapidly growing list—e.g., GDPR, CCPA/CPRA (California), PIPEDA (Canada), HIPAA—demand protection of personal and sensitive data. They do allow data sharing when there are appropriate safeguards in place. When protections are guaranteed without reverting to legal agreements, regulatory challenges are reduced or eliminated.
- Third-party data risk eliminated
Lax cybersecurity at third-party firms has become a significant threat in recent years. When your data is held under trust by a third-party, a compromise of their systems directly compromises your data too. Under traditional approaches to sharing data between firms, even when bound by specific requirements about data security precautions, a shortcoming in their implementation of security controls—while not technically your responsibility—can implicate your data when they suffer a data leak, data breach, or insider attack. Secure data collaboration—where data is shared using privacy-enhancing technologies—virtually eliminates the risk that a cybersecurity incident at a trusted third-party firm will become a nightmare for yours.
Zero Trust Data Collaboration
Zero trust network architectures have become a significant trend in security circles, offering a new approach that re-thinks security as more than protecting the perimeter. In our research on zero trust last year, we commented that most organizations were putting too little focus on the fundamental data disciplines of zero trust, such as data audits, data classification, and data flow management. To that analysis from last year, we would add the demand to investigate the use of new approaches to data collaboration. Privacy-enhancing technologies enable collaboration on fully encrypted data sets, eliminating the trust condition from data collaboration agreements—or in essence, enforcing cross-organizational zero trust on data of interest to multiple parties.
___________

Michael is the Senior Research Analyst at Osterman Research, with broad interests in cybersecurity, data protection and information governance. Michael prepares survey reports and white papers for new projects, coordinating their completion through to publication.
Michael is the author of seven books on collaboration and user adoption, including Re-Imagining Productive Work with Office 365, User Adoption Strategies (2nd Edition), and Collaboration Roadmap.
Michael holds a Master of Commerce with first-class honours in telecommunications-based IT from the University of Canterbury in New Zealand. In his spare time, you will find Michael putting in lengths at the local swimming pool.